A Journey Through Directory Bruteforcing using ChatGPT
As a security researcher, I have been consistently fascinated by the United States Government’s Vulnerability Disclosure Program, an initiative aimed at identifying and fixing security vulnerabilities in government systems. To delve deeper into this program, I started my research with a certain law enforcement agency. Their Vulnerability Disclosure Program has been active since August 2020, with the primary goal of ensuring the security of the systems and websites managed by the organization, protecting them from cyber-attacks. This program allows individuals and organizations, including security researchers, to report any vulnerabilities they discover in the organization’s systems.
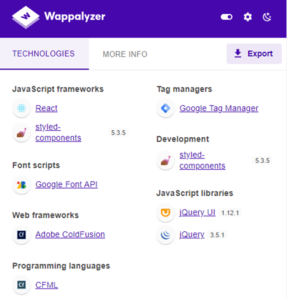
Without delving too deeply, I initiated a directory brute-forcing attack using SecList’s ‘Quickhits’ against the root domain. The ‘Quickhits’ list is a dictionary of common directory names found on websites, helping identify hidden pages. During this process, I stumbled upon a redirect on the ‘/Admin’ directory, which led me back to the login page, indicating possible access to an ‘administrator’ page. Wappalyzer identified the web application as being built with ColdFusion, prompting me to search for wordlists designed specifically for this platform. I found the updated ‘OneListForAll’ list on Github, which not only included wordlists for ColdFusion but also other technologies.
Below is a screenshot of technologies identified on the website.
Continuing my directory brute-forcing within the ‘/Admin’ directory, I received a ‘500 status’ code on ‘/dialogs.cfm’, suggesting a potential directory or server-side configuration error. Seeking guidance on common parameters in ‘dialogs.cfm’, I turned to ChatGPT, which provided me with a list of commonly seen values for the dialog parameter.
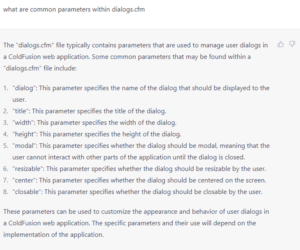
Instead of navigating through multiple word lists, I consulted ChatGPT again to determine commonly seen values with the dialog parameter. With only seven values, I tried each one in my web browser, leading me to the ‘/Admin/dialogs.cfm?dialog=SelectUser’ endpoint.

This granted me access to an administrator endpoint that displayed sensitive information for facility managers across various U.S. government agencies. The information included 638 email addresses, names, and unique usernames. Unfortunately, I cannot provide a screenshot of this data, so you’ll have to imagine the details.
The organization’s quick response to a recent vulnerability demonstrated its commitment to ensuring system security. The rapid resolution time, just five days from vulnerability submission to fix release, underscores the agency’s proactive security approach and efficiency in addressing threats. This incident highlights the importance the agency places on securing its systems and data.
Why was such a significant vulnerability overlooked?
While several factors may contribute, the primary reason likely lies in automated scanning tools’ limitations to detect hidden pages and endpoints, as well as their inability to check for authorization controls. Even if these tools identified hidden pages, they might not have determined if an anonymous user had necessary permissions for specific endpoints. In this case, the endpoint ‘/Admin/dialogs.cfm?dialog=SelectUser’ was accessible due to inadequate authorization controls, leading to unauthorized access to sensitive information. This common issue emphasizes the importance of robust authentication and authorization controls in preventing unauthorized data access in web applications.
How should this application be assessed moving forward?
Moving forward, assessing this application should involve comprehensive methodologies outlined in the OWASP Web Security Testing Guide (WSTG). These steps include reconnaissance, attack surface mapping, configuration testing, authentication and authorization testing, data validation testing, cryptographic storage and transmission testing, business logic testing, and error handling and verbose information testing. Testers should be provided with credentials for each role to validate proper roles and permissions.
Coastline Cybersecurity, with its expert team and cutting-edge technology, offers comprehensive security assessments that can identify vulnerabilities in even mature security models. Their experience enables quick and effective risk detection, helping clients defend against cyberattacks, secure networks, protect sensitive data, and ensure regulatory compliance. Let Coastline Cybersecurity help you find vulnerabilities before they become problems.
